Today organizations and companies throughout the world are moving towards technological enhancement as almost all industries are accepting the technological aspects, this position makes cyber security an important aspect that cannot be overlooked in any organization or company, no matter the size of this company or organization. From the above networks threats are on the rise and as is evident most of the time, they are doing new things, more of a complex nature, and hence there is need for the security experts to move to the next level of knowledge.
The only one that was recognized in cybersecurity is the MITRE ATT&CK Framework. For all the kinds of people engaged in the cybersecurity industry, particularly the cybersecurity analysts, the most valuable resource for comprehensively categorizing adversaries and devising safeguard mechanisms to counter threats are the knowledge resources that the MITRE ATT&CK Framework has to offer. In this article, it is going to dive further into details regarding the MITRE ATT&CK Framework and with these knowledge, one can transform from being an average user of cybersecurity to being a hero.
What You’ll Learn
1. Comprehensive Understanding of MITRE ATT&CK
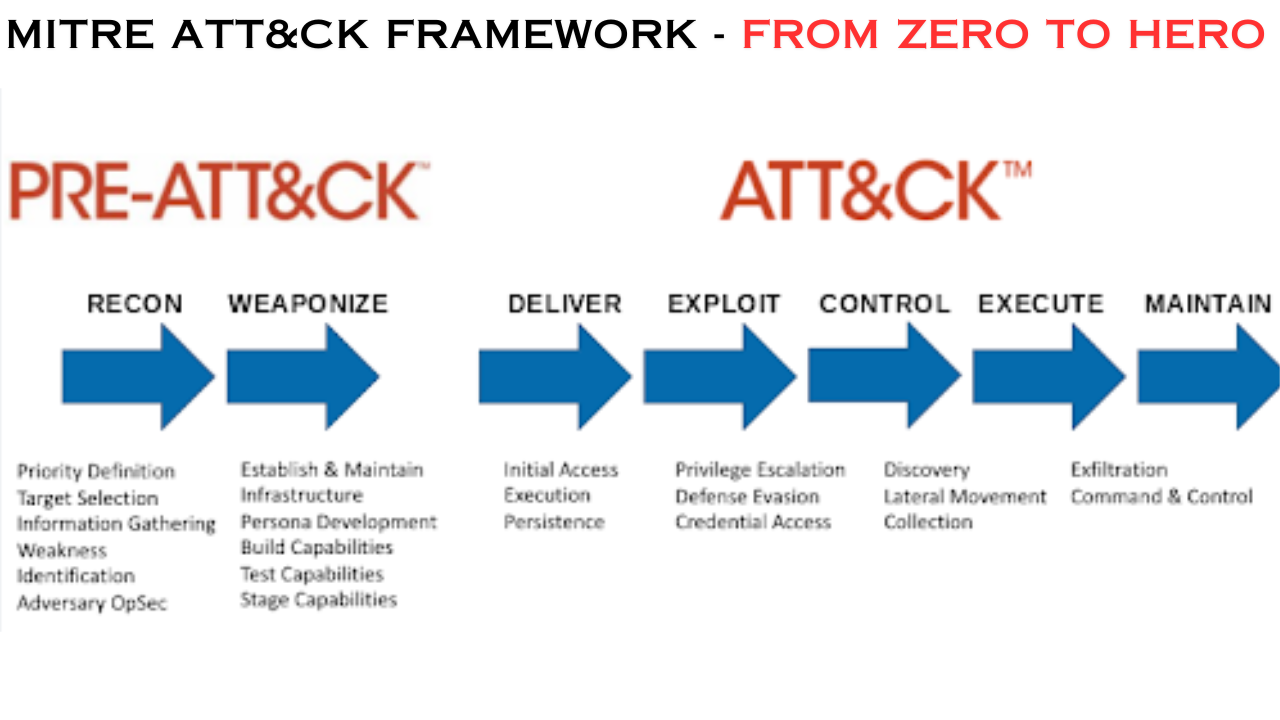
But if we are going to arrive at details concerning the MITRE ATT&CK Framework, one must first get an understanding to what this idea refers to. ATT&CK is the short form of Adversary Tactics, Techniques & Common Knowledge, which is a knowledge base that has been developed by MITRE – the Massachusetts Institute of Technology Research and Engineering organization – that systematically defines all possible strategic movements and often-staged actions an adversary might take in the real world.
2. Effective Identification and Analysis of Cyber Threats
It is for this reason that understanding the purpose and utilization of the MITRE ATT&CK Framework is paramount in the world of cybersecurity. Being an extensive structure of the tactics along with the respective techniques and sub-techniques, the framework helps to follow a systematic course when it comes to threat analysis. Here, by making oneself acquainted with these elements, one is capable of identifying typical actions of threats and, consequently, would be able to prevent possible security incidents.
3. Understanding Typical Behavior Patterns of Adversaries
Since attackers are always out to wreak havoc on systems and networks, they will exhibit certain behaviors when launching cyber attacks. These patterns portray how a particular form of vulnerability can be exploited thus assisting the cybersecurity professionals to guard against high risk areas. The MITRE ATT&CK Framework gives valuable information about a typical behavior of the adversary to facilitate avoiding the occurrence of an attack in the first place.
4. Application of MITRE ATT&CK Framework in Real-World Scenarios
Most certainly, theoretical backgrounds have their importance, but it is within the sphere of applicability that the MITRE ATT&CK Framework really shines. Therefore, in real-world conditions, cybersecurity experts can utilize the framework for the evaluation of security and the improvement of the concepts associated with cyber defense. Through tailoring the framework for your organization, the potential cyber threats that exist in the organization will be easily identified and dealt with efficiently.
5. Engage in Interactive Exercises and Real-World Case Studies
One can only learn the MITRE ATT&CK Framework practically by practicing it or encountering it firsthand. Activities based on realistic events, scenario- and case-based exemplifications effectively incorporate the framework in real cyber lead situations and threat-hunting. They are intended to help you foster practical experience and enhance your ability to utilize the framework towards solving real life cybersecurity issue.
6. Learn Strategies to Stay Updated with the Cyber Threat Landscape
Modern threats increase gradually pace and the subject of cybersecurity is rather dynamic as a result. Given the ever-evolving threats in the field of cybersecurity, those personnel have to renew their knowledge and skills periodically. The MITRE ATT&CK Framework helps users to learn timely information and various approaches for counteracting threats within the contemporary information space. When applying these strategies into your cybersecurity attempt, you assure yourself of being a better prepared and proactive contender when it comes to the ever evolving threats in cyberspace.
7. Develop Essential Skills for Collaborating and Communicating Effectively
Introducing The communication and collaboration model that has been developed to help cybersecurity professionals to release their interpersonal interaction with other members of an organization, adequately adapted to accommodate the complex and dynamic working environment. in the Strategy section of the MITRE ATT&CK Framework, there is a focus on the actors involved and the cooperation and communication. When doing so, you will help to ensure you have the essential collaboration skills needed to align cybersecurity risk and technical controls across your organization.
8. Advanced Threat Hunting Techniques
The real icing on the cake is the fact that as you navigate through the MITRE ATT&CK Framework, you will discover more detailed attack tactics to implement in your threat hunting process. These techniques help you to act on the threats in the same way as you want and deter them before they become full scale cyber attacks. This way you can sharpen your threat hunting skills within the context of the framework ad track down minor signs of an attack that may lead to taking physical measures to protect an organization’s resources.
9. Integration with Security Tools and Technologies
For any security analyst to benefit extensively from the MITRE ATT&CK Framework, it is recommended that the analyst incorporates the framework alongside his/her organization’s security products. Applying APIs and integrating them generates effective methods for threat management and identification, as well as helps improve the structure of work with anti-virus incidents. When you comprehend how the main concepts can be combined with security technologies, you can unleash huge potential to repel cyber threats.
10. Continuous Improvement and Optimization
Cybersecurity is an ongoing process and it is not a one hundred fully secured event and it requires constant tweaking and working out. Through the utilization of the MITRE ATT&CK Framework, individuals and organizations can foster ongoing improvement by adopting well-structured and effective cybersecurity strategies. In this way, the cybersecurity continually is revised and updated in the framework together with other aspects related to the organization so that it evolves in time and no new threat overwhelms its defenses.
11. Certification and Recognition
The implementation of the MITRE ATT&CK Framework may result in accreditation within academic circles or cybersecurity industry. The framework is beneficial in organisations, and thus, individuals with the following competencies are appreciated: Certification is a way, through which you could affirm the quality, dedication, and readiness to improve and protect your company along with ensuring that you become a reputable figure in the field of cybersecurity.
12. Contribution to the Cybersecurity Community
When moving on to the next level of your understanding of the MITRE ATT&CK Framework, it should be beneficial for everyone involved to get involved with the cybersecurity community and share the findings. Engage in online discussion groups, seminars and workshops to meet and discuss with other professionals, review case studies, and discover new strategies that have been used to identify threats and prevent or minimize the damage that may arise from them. Thus, not only will you act as a contributor to the framework and strengthen it yourself, but you will also contribute to other people’s journey to becoming cybersecurity heroes.
In conclusion, becoming an expert in the MITRE ATT&CK Framework is one of the most valuable professional developments that cyber-security specialists can be heroes in their companies today. You will be therefore prepared and poised to effectively counter the threats by following the following important tenets: comprehensively understanding the framework, mastering advanced threat hunting techniques, integrating the framework into security tools and technologies, creating a culture of improvement and innovation, attaining certification and recognition, and participating in the cybersecurity knowledge base.
Conclusion
In the latest trends of cybersecurity, the MITRE ATT&CK Framework can be considered as a direction that illuminates the way. Since its establishment, it has equipped cybersecurity professionals with the knowledge and tools they need to effectively address the unrelenting challenge of cyber threats. In this way, the SECI framework enhances the efficiency of threat identification and offers precautionary measures that have turned ordinary workers into tactical cybersecurity supporters.
The following are some of the implications of utilising, or adopting the MITRE ATT&CK Framework: Those who adopt the MITRE ATT&CK Framework are on a never-ending learning process. This way from novice level up to becoming the hero that navigate through the complex terrain of the adversary’s strategies, and those of the tactics, techniques and procedures as well as analyzing and responding to threats. The overall optimism and tenacity demonstrated in the lives of Taylor and Ben make them more determined to counter whatever barriers life throws at them.
However, the new threat vectors that are developing in the cyber space indicates that we have to move with the same pace in order to address the new challenges that are coming up. MITRE ATT&CK Framework reveals the best practices on how to adapt and innovate in the field, serving as a roadmap towards mastering cybersecurity for professionals’ desire to stay on top of their game. It might concern or discuss collaboration, communication, and common goals that we have to face all hands down every challenge that may be on the way.
So you see, it is not the titles or certifications as to who leave a clear definition of a cybersecurity hero, but it’s the spirit that they bring in defending the virtual world. That is why using the knowledge and tools of the MITRE ATT&CK Framework, they remain as envoys who protect the cyberspace from those who wish harm towards it.
FAQ :
Why is the MITRE ATT&CK Framework important?
The importance of the MITRE ATT&CK Framework is in the fact that it offers a clear model to use when addressing threats within a technological environment and the roles of cybersecurity experts. This is due to its detailed matrix of tactics and techniques which if understood together with the behaviour patterns of adversaries, will lead to a improved protective capability within an organizations’ cybersecurity strategy or plans.
How can I learn to use the MITRE ATT&CK Framework effectively?
To conduct information security professionals and cybersecurity teams in transferring the knowledge in practice, such persons can undergo training from MITRE or other institutions through courses, workshops, and online tutorials available to MITRE. He also lists extra possibilities of enriching the apprehension and expertise of the framework through, for example, hands-on exercise, case studies, and cooperative experiences among peers in the cybersecurity industry.
What are some common use cases for the MITRE ATT&CK Framework?
Organizations use the MITRE ATT&CK Framework for tasks such as threat hunting, situation analysis, red-teaming, security assessment, and improving overall defense tactics. This specific approach can be used in any given cybersecurity environment in order to detect, and examine, as well as rectify threats to cybersecurity.
Is certification available for the MITRE ATT&CK Framework?
As of now, there is no special certification that would be awarded for the MITRE ATT&CK Framework. However, individuals can gain accreditation and endorsement of their competence with the framework, by enrolling in various training exercises, accomplishing practical assessments, and engaging within the cybersecurity parametric.