It is very important for people to stay safe online from cyber attacks as their Cyber Security has become so much at risk. They can impact the economy in a negative way in that, they can result in to loss of valuable information, interruption of services, and destruction of infrastructure. Here, it will be crucial to mention some of the most typical forms of concern since knowing one’s enemy is half the battle.

1) Malware Attacks
Malware is somewhat like a virus intrinsic to digital devices including computers. Malware can take advantage of an opening in your comptuer through e-mails, downloads, or popular websites. Once inside, it will be able to either pilfer your information, monitor your activity or even corrupt the contents of your files.
Malicious programs are algorithms that can harm your computer or device in a similar way as a virus infects the organism. They arrive unknown through the inbox, through downloads, or websites, with malicious intent to compromise data and settings. Once inside, they can hack your computer, steal files or perform actions on your behalf.
There are always potential threats online which is why it’s vital to take precautions and secure yourself by avoiding clicking on unknown links or downloading files, using anti-virus, and ensuring all your devices are up-to-date. With some premeditating and preventing principles, candidates can minimize the series of receiving malware Cyber attacks and enable a safe internet experience.

2) Denial-of-Service (DoS) Attacks
A Denial-of-service attack is similar to road jam where the internet traffic slows down or even hinders website and network performance. Thes are kinds of cyber attacks where hackers inundate a website or a nonet with traffic, like cars clogging a highway.
This sheer number of activity overwhelms the website or the network, thereby denying real users the ability to penetrate the site. It is like there being more people pushing through a door at the same time, then blocking the door with their bodies and mass making it impossible for other people to walk through the door.
Surely, it very dangerous to make DoS attacks because mishandled it can really create big issues. They can bring a website down, cause mobile and online applications to stop working, or completely knock a networks off line.
Consider being at the airport and finding out you cannot board a plane to reach your dear ones because the airline is under cyber attack!
General shields that Websites/Networks have towards DoS attacks are as follows. These defenses can filter the fake traffic and prevent it from being detrimental to the system. Basically they are similar to security personnel posted at strategic positions to act as watchdogs to prevent mischievous individuals from creating havoc.
Exploring the details of DoS attacks enable me to appreciate why cybersecurity is crucial. It also serves as a message that tells people to be cautious while on the Intenrnet and to guard themselves against internet dangers. Let us educate ourselves as well as use effective methods to observe and control what happens on the internet thus making the world a better place.

3) Phishing Attacks
Phishing cyber attacks are in fact a form of internet pranks that lure people into revealing their details. The criminals imitate themselves, and it looks as if they are sending e-mail messages or messages from authentic sources like banks, companies etc. These messages could be requests for account information such as passwords, or card details such as credit cards. It is as if any fisherman, out to catch a fish, throws the bait to the water in anticipation that someone will go for the bait.
Whenever an individual subscribes to such links and provides their details, then con artists can exploit the details and intrude into the victim’s Individual Accountability Number, financial account, and among other things. It can also be likened to inviting a complete stranger into your house then offering to hand over the house keys to them.
Therefore to avoid these, one should be way alert as much as it is possible. Use the header field to pay attention to sender’s actual address and avoid clicking on emails that seem to be phishing attempts, like mistakes in spelling and urgent letters concerning your personal data. No matter how inviting a link might appear, or how friendly an e-mail might seem, do not trust them and give out any information without confirming whether what you’re doing is safe or not. It is therefore wise if one is able to be careful and able to avoid anything that looks like a phishing cyber attack so that one is able to protect his or her information from being hacked or stolen online.
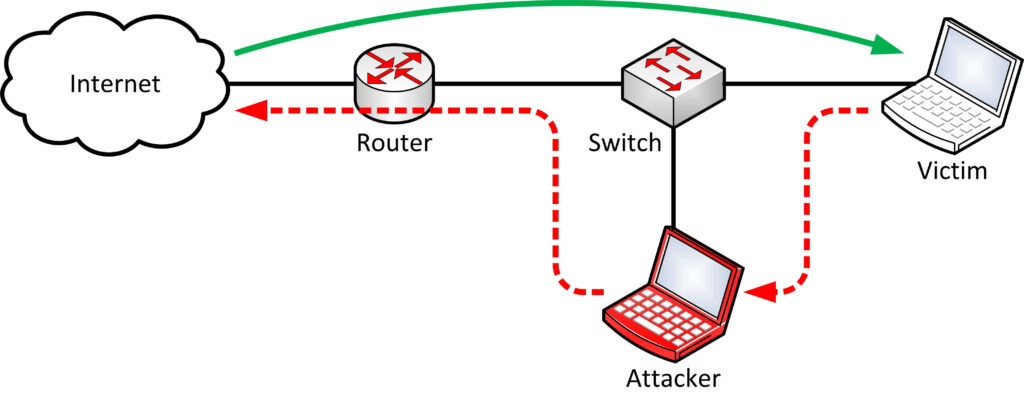
4) Spoofing Attacks
Otherwise referred to as identity theft, spoofing cyber attacks are akin to put on in the digital world where hackers portray events that aren’t true with the intention of deceiving others for their malicious gains. These cyber attacks involve the cyber attackers impersonating the character of a trusted person, website or company.
Scammers may pose as legitimate senders with fake email addresses or by creating sites similar to genuine websites. It is as deceptive as a person disguising themselves to become a friend with the aim of mugging someone.
If they manage to lure you into trusting them, then you are most likely going to disclose your identity, and they will then guide you through to follow malicious links. For instance, they may use an email that looks like it has been sent by your financial institution and request for details of the account. If harassed, it could trick you into losing your money or personal details.
To prevent spoofing, be wary of the messages that you receive with the unknown senders. Be extra vigilant for any changes, such as different addresses with tiny typographical differences or web addresses that look correct but are in fact slightly altered. Always be cautious if there is something that you find strange because it could be a scammer if you need to check your identity go ahead and do so with an authorized personnel. As you have learned from this course, one can easily be a victim of spoofing cyber attacks and this means the need to be vigilant and avoid losing sensitive information.

5) Identity-Based Attacks
Identify based cyber attack is like covert attack with predicted targets based on the identity of the victims. The hackers appear to spy on their target, their lifestyle, friends, or even personal information about them. It is more like one who is following you in order to discover what you do not want them to know.
Once hackers have enough information, in fact, they can also get into more personal levels of ‘probe’, like faking an e-mail or a fake website. For example, they might disguise themselves as a friend or co-worker with the aim of misleading you and obtain some personal details about you. Embedded operating systems are a comparable example; they will mimic another operating system to make it seem as though they are that operating system.
They cause identity theft, financial loss, and in extreme cases, harm to reputation of organization or business. When engaging in such cyber attacks, you should bear in mind that it is dangerous to reveal your identity on social media networks. Report emails or messages that are extremely unusual or seem suspicious as they might not be genuine. Moreover, one has to learn to set his privacy on his accounts and also change passwords every now and then.
So being conscious and careful of data that is posted online, can greatly minimize the chances of having an account hacked via an identity cyber attack, and ultimately protecting your identity while online.

6) Code Injection Attacks
These are like intruders entering a house through fractures that are invisible to the inhabitants of a house. These are attacks where a hacker takes advantage of weak or unsecured areas within an application or a website by embedding or implanting a code that is not authorized by the owner of the site. There has always been a whisper of feedback – as if ideas were communicated through a two-sided letter placed in the crack between two boards.
Once the malware gets in, the hacker might have their way with stolen data, website or application control, or Malware propagation to users. It is similar to the he being in your room and taking whatever he wanted without you realizing that it was being done.
These attacks can lead to various consequences, whereby personal accounts, corporate websites, and databases, among others may be exposed to hacking, viruses, and other related malicious attacks. The most common prevention methods include constantly updating the software and adding defensive measures, as well as incorporating security into the coding process. Web users must also be careful when they are accessing a particular site or an application, they should not open suspicious links or download anything.
Therefore, to avoid being a victim of a code injection attack, the adequate measure one should take to avoid this form of cybercrimes is to always follow updates on the various attacks and take the necessary precautions in order not to be a victim of cyber criminals’ malicious deeds.
7) Supply Chain Attacks
Supply chain attacks are as if the opponent moved unnoticed and gained access to a building by entering through the backdoor provided by contractors and suppliers. In these attacks, the hackers direct their activities to organizations that are contracted by other parties to offer software or a service. It’s like something ‘crawling through the back door – they didn’t get in through the front, nor did they come in through the front door.
Once inside the corporations, they can inject malicious code or tamper with the computers. This enables them to infect all clients who use the contaminated software or the given service. For example, it is like poisoning a vendor of foodstuffs in a bid to affect all who take the foods.
It is partly because of these attacks that one organization’s customers can be significantly impacted, along with customers of other organizations. To avoid supply chain attacks, organizations should also scrutinously oversee suppliers and guarantee adequate protection solutions for sellers. Users should also remain even more cautious and make sure that the software installed is updated all the time, fixing these holes.
Understanding the extent of dangers which arise from the supply chain attacks and acting in advance by decreasing their potential threats performing organizations will comparatively have fewer chances to become victims of these well-advanced cyber-attacks.

8) Insider Threats
Insider threats are actual or potential security risks posed by individuals already within an organization or its contractors or business partners who knowingly or intentionally engage in abusive acts. This may range from cases of employees just embezzling information to handling a grudge and sabotaging processes. It has to be like a commercial that makes you trust and buy, and then turn around and become unfriendly.
9) DNS Tunneling
DNS Tunneling is similar to the conveyance of messages hidden in plain envelopes; messaging amidst standard web traffic. Haiyaks is one such attack which uses the DNS to go through the miscellaneous measures and can carry on talks clandestinely. It’s like placing a message inside an analogy where there exists a multitude or similar analogies for people to find in comparison.
A hacker can insert information into DNS queries or responses, and hence, send original or stolen data from a compromised network or computer to an external server undetected. It is as if I’m just exchanging messages to and fro without anyone paying any attention to me.
To minimize the effects of DNS tunneling, organizations should set up the traffic that passes through the DNS server for any activity that appears to be in a form of tunneling and set measures to block such channels.
10) IoT-Based Attacks
Targeted smart Internet of Things such as thermostats and watches and cameras are attacked. Criminals take advantage of these holes to penetrate into networks or stage rudimentary attacks. It is, of course, similar to a thief entering a house through an open window.
If the hackers infiltrate the device, they can either run it or use it to initiate other bigger attacks such as identity theft or distribution of malicious software.
For security against IoT attacks, users must reset passwords, ensure IOS firmware updates, and deploy WPA2 encryption for their wireless networks. Thus, by following these measures, citizens can protect their smart devices and equally do not allow the criminals exploit them.
Preventive Measures from Cyberattacks
To stay safe from cyber attacks, we should do few things like first, we make sure our computers operating system is up to date. This helps us fixing any weakness that attackers might use for intrusion. Also get a good antivirus software. It’s like a Guard that stops bad software from getting into your computer.
Next make sure strong passwords with numbers, letters, and symbols should be used change them regularly so that it’s harder for attackers to guess them. We should use security tools like Firewall intrusion detection system to keep our computer safe when it’s connected to the internet.
We should back up our important data regularly, so if something bad happens or any attack happens, we will not lose everything when you are on the internet. Then we should use a VPN to make it harder for hackers to see what we are doing.
We need to be careful with emails from people. You don’t know. Sometimes they can have malicious software in them. Avoid using public Wi-Fi because it’s not very safe. Make sure your Wi-Fi at home is protected with a strong password.
Teach your team and employees to stay safe online , organise regular information security training for the employees. Phones and tablets needs protection too so treat them like computers. Only download apps from trusted platforms only and use extra security measures like multi factor authentication for importance softwares.
Conclusion
Cyber attacks exist in different categories but making sure that one learns the basics of these cyber attacks will assist one in reducing the risks of contacting them. Therefore, acclimatizing oneself with these general risks and ensuring that necessary precautions are in place and effect can help cut the chance of being a cybercrime’s next victim. Still, always make sure that your software is up to date, choose complex passwords and do not click on the links and provide information that can be hardly considered safe.
FAQs
Q: What is a cyber attack?
A: Cyber attack can therefore be described as a deliberate attempt to compromise the digital integrity of an individual, a group or even organization’s networking and information processing systems. A cyber attack can be defined as a planed attack on an organization’s computer system and the data or information it processes including through the internet.
Q: What are the common types of cyber attacks?
A: It is imperative to know the kinds of cyber attacks that are most frequently reported: Common forms of cyber attacks are; Malware attack would include virus, worms and ransom-ware, phishing attack, Denial of Service (DoS) and Man-in-the-middle attack, SQL injection attack as well as Zero-day attack.
Q: What is a malware attack?
A: I think it makes sense to begin with the definition of the term that is met quite often in the modern world full of computers and technologies, a Malware attack. Malware attack can be defined as a situation where someone else breaks into a computer system or damages it with the use of vile software. Some of the classifications of malware include viruses, worms, Trojan cat, ransomware, and spyware.
Q: What is a phishing attack?
A: Phishing can be defined as identity theft or threats assisted by deceit where fraudster tries to trick the lady or man he or she has met for the first time to provide him/her with personal information such as user name, password or credit card number. The initiation of most of the phishing scams begins through the use of email, messages on the portable devices, or through calls.
Q: What is a denial-of-service (DoS) attack?
A: A denial of service attack is a network or a computer system attack on a website or application and is aimed at depriving the legitimate users the right to access the services they intend to use by submitting messages or requests that are invalid or flooding the network and users with the same.